When it comes to cybersecurity, data encryption is one of the most important practices you can implement. As our world becomes increasingly digital, safeguarding sensitive information has never been more critical. Whether you’re a business owner, an IT professional, or simply someone looking to protect your personal data, understanding and applying best practices for data encryption is crucial.
In this article, I’ll walk you through the essential best practices for data encryption in cybersecurity, explaining key concepts, outlining important strategies, and offering actionable advice that you can implement right away to protect your data from hackers and unauthorized access.
Key Takeaways
-
Data encryption is essential for protecting sensitive information from unauthorized access.
-
Encrypting data both at rest and in transit ensures comprehensive protection.
-
The best encryption practices involve strong algorithms and proper key management.
-
Compliance with industry regulations, such as GDPR and HIPAA, requires encryption to safeguard data.
-
Implementing multi-factor authentication adds an additional layer of security to your encryption efforts.
What is Data Encryption?
Before diving into the best practices for data encryption in cybersecurity, let’s first understand what data encryption is. Simply put, data encryption is the process of converting information into a code to prevent unauthorized access. This is done using algorithms that scramble the data, making it unreadable to anyone without the correct decryption key.
In cybersecurity, encryption plays a crucial role in securing both data at rest (stored data) and data in transit (data being transmitted over networks). Without encryption, sensitive information such as passwords, credit card numbers, and personal identification details would be vulnerable to cyberattacks.
Why is Data Encryption Important in Cybersecurity?
Data encryption is the first line of defense against cybercriminals. Here’s why it’s important:
-
Prevents Data Breaches: If your data isn’t encrypted, it’s easier for hackers to access and steal it.
-
Compliance Requirements: Many regulations, such as GDPR, require encryption to protect user data.
-
Protection in Transit: Data traveling over the internet is exposed to many threats. Encryption ensures that even if it’s intercepted, it’s unreadable.
Best Practices for Data Encryption in Cybersecurity
Now that we understand why data encryption is important, let’s discuss the best practices for data encryption in cybersecurity that you should follow.
1. Use Strong Encryption Algorithms
One of the first best practices for data encryption in cybersecurity is to use strong encryption algorithms. AES (Advanced Encryption Standard) is widely regarded as one of the most secure encryption algorithms available. It is used by the U.S. government for encrypting classified information and is widely accepted across industries.
It’s important to choose an encryption algorithm that is both secure and well-supported. Avoid older algorithms like DES (Data Encryption Standard) as they are outdated and can be easily compromised.
Common Encryption Algorithms
| Algorithm | Key Length | Strength |
|---|---|---|
| AES (Advanced) | 128, 192, 256 bits | Very Strong |
| RSA | 1024, 2048, 4096 bits | Strong, widely used |
| DES | 56 bits | Weak (outdated) |
| Blowfish | 128 bits | Moderate |
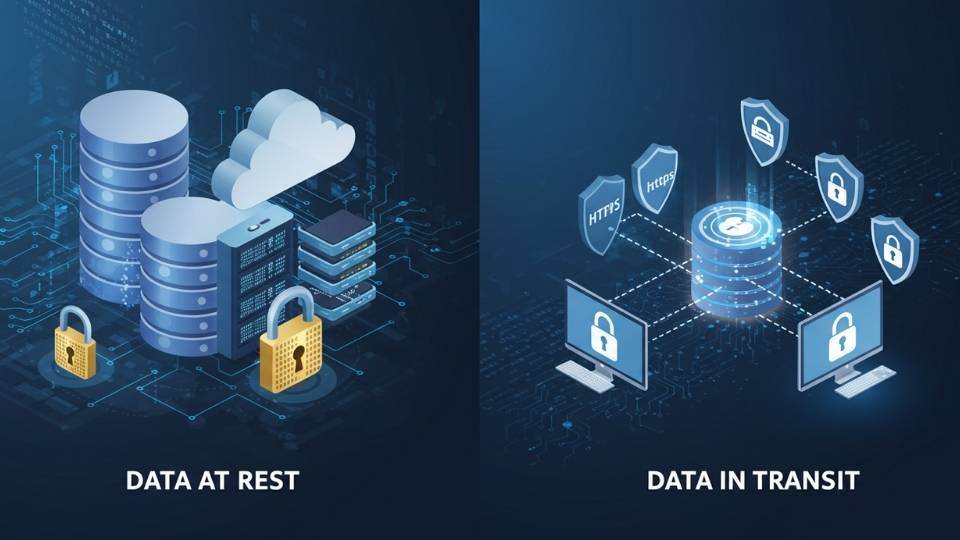
2. Encrypt Data Both At Rest and In Transit
Data encryption is not just about encrypting data stored on your device (data at rest). It’s also important to encrypt data while it’s being transmitted over networks (data in transit). By encrypting data both at rest and in transit, you ensure that your sensitive information is protected no matter where it is.
-
At Rest Encryption: This type of encryption is used for data stored on hard drives, databases, or cloud servers. It prevents unauthorized access if someone gains physical access to the system.
-
In Transit Encryption: This type of encryption secures data when it’s moving between devices or servers. It’s commonly used with secure protocols like HTTPS (Hypertext Transfer Protocol Secure) and TLS (Transport Layer Security).
3. Manage Encryption Keys Securely
Encryption keys are what turn encrypted data into readable information. Managing your encryption keys securely is critical to maintaining the integrity of your encryption efforts. Losing or mishandling an encryption key can result in permanently losing access to your encrypted data.
Here are a few tips to manage your encryption keys effectively:
-
Generate strong keys: Always use long, random keys.
-
Store keys securely: Use key management systems (KMS) or hardware security modules (HSM) for storing encryption keys.
-
Rotate keys regularly: Periodically change your encryption keys to mitigate the risk of them being compromised.
Best Practices for Key Management
| Key Management Tip | Description |
|---|---|
| Use Strong, Random Keys | Avoid predictable keys. Use key generators. |
| Store Keys in Secure Locations | Use encrypted storage for keys. |
| Rotate Keys Regularly | Periodic key rotation ensures better security. |
4. Implement End-to-End Encryption
End-to-end encryption (E2EE) ensures that data is encrypted on the sender’s side and only decrypted on the receiver’s side, preventing anyone in between from reading the data. This is particularly important for messaging apps, email communication, and file sharing.
Many communication platforms like WhatsApp and Signal use end-to-end encryption to protect user privacy. It’s essential to implement E2EE wherever possible to ensure that your data stays secure even in transit.
5. Use Multi-Factor Authentication (MFA)
While data encryption secures your data, multi-factor authentication (MFA) adds another layer of protection by requiring more than just a password to access encrypted information. With MFA, a user must provide two or more verification factors, such as:
-
Something they know (password),
-
Something they have (a smartphone app for verification), or
-
Something they are (fingerprint or facial recognition).
MFA helps protect encrypted data from unauthorized access, even if someone gains access to the encryption key.
Common Pitfalls to Avoid in Data Encryption
Although encryption is a powerful tool, it’s essential to avoid some common mistakes that can compromise its effectiveness. Here are some pitfalls to be aware of:
1. Using Weak Encryption Keys
Weak encryption keys are easier for attackers to guess or crack. Always generate long, random keys that are difficult to predict.
2. Inconsistent Encryption Across Systems
Make sure that your encryption practices are consistent across all systems and devices. If some systems are not encrypted or use weak encryption, your entire network could be vulnerable.
3. Mismanaging Decryption Keys
Losing or mishandling decryption keys can prevent you from accessing your encrypted data. It’s critical to securely store and manage these keys.
Data Encryption and Regulatory Compliance
Many industries have regulatory requirements that mandate data encryption. For example, GDPR (General Data Protection Regulation) and HIPAA (Health Insurance Portability and Accountability Act) require organizations to implement encryption to protect personal data.
Ensuring that your encryption practices align with these regulations not only helps protect your data but also keeps your business compliant with the law. Failure to do so can result in significant penalties and reputational damage.
Regulatory Compliance and Encryption Requirements
| Regulation | Encryption Requirement | Industry |
|---|---|---|
| GDPR | Requires encryption for personal data | General Data Protection |
| HIPAA | Encrypt patient health information | Healthcare |
| PCI-DSS | Encrypt credit card data | Payment Processing |
The Future of Data Encryption
As technology continues to evolve, so do the threats to data security. The rise of quantum computing poses a potential challenge to current encryption standards, but the field is already working on post-quantum cryptography to create encryption algorithms that can withstand quantum attacks.
In the coming years, we can expect to see new encryption methods that are better suited to combat emerging cyber threats, while still protecting sensitive data.
My Opinion
In conclusion, data encryption is one of the most effective ways to protect your sensitive information from unauthorized access. By following the best practices for data encryption in cybersecurity, such as using strong encryption algorithms, managing encryption keys securely, and implementing end-to-end encryption, you can significantly reduce the risk of data breaches.
Remember, data encryption is just one part of your cybersecurity strategy. It should be combined with other best practices, like regular software updates, firewalls, and multi-factor authentication, to create a robust defense against cyberattacks.
Taking action now to encrypt your data can save you from potentially catastrophic consequences later.
















Leave a Reply